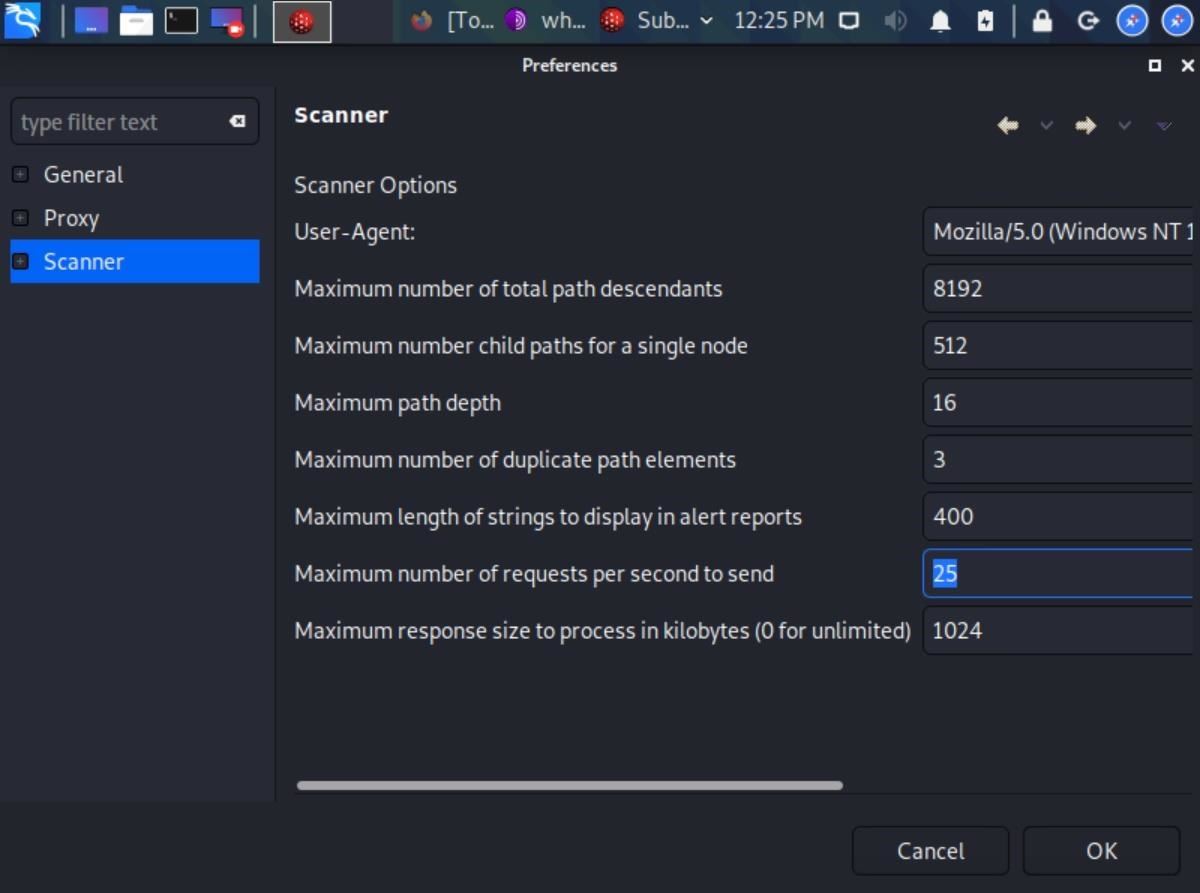
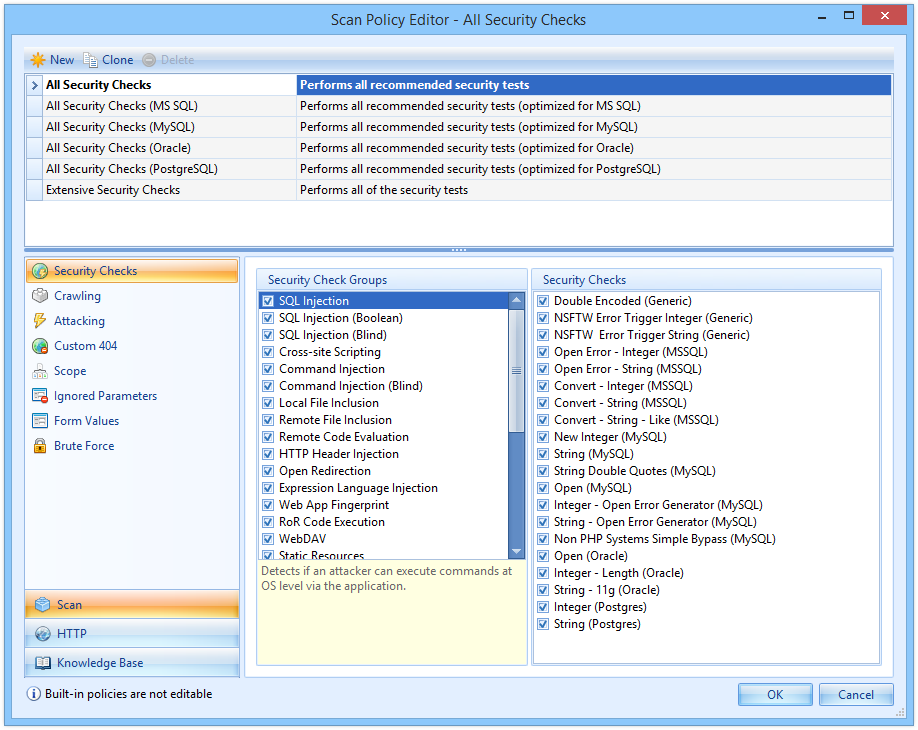
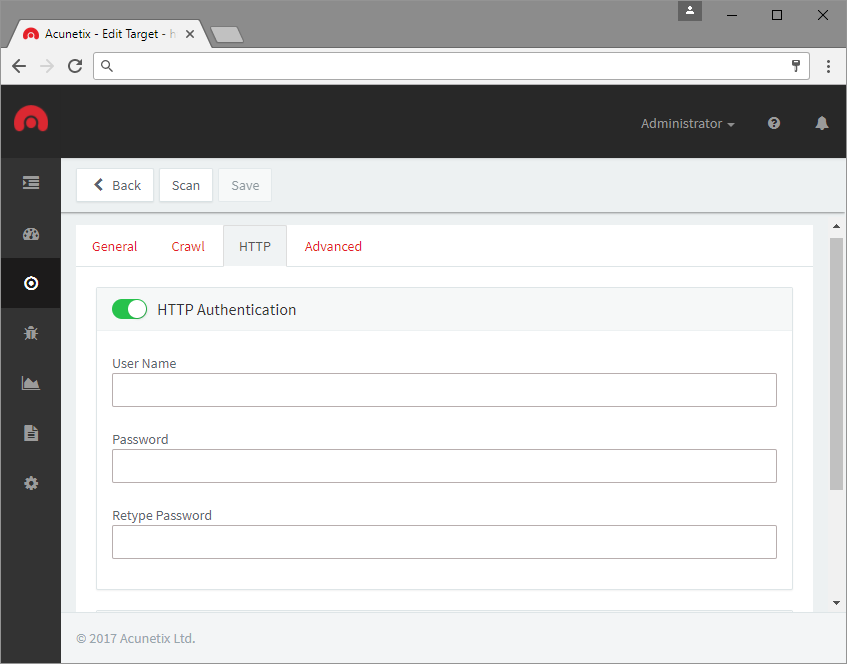
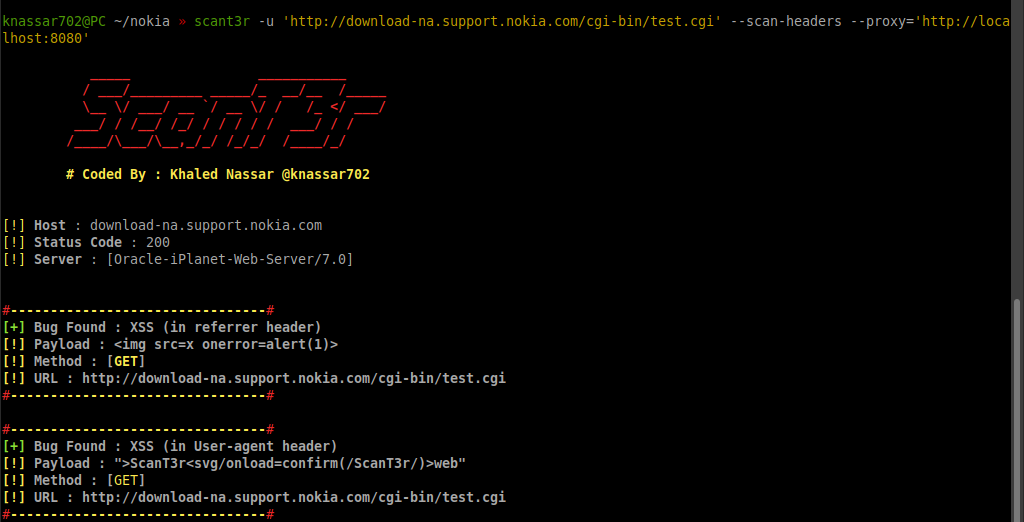
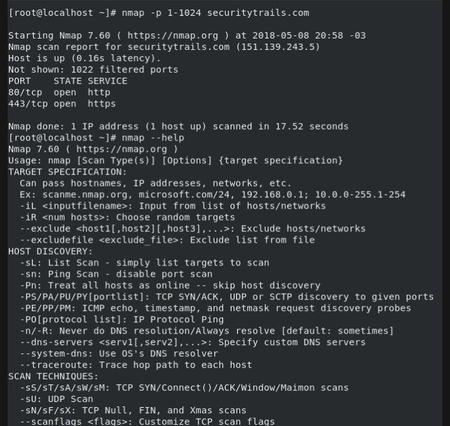
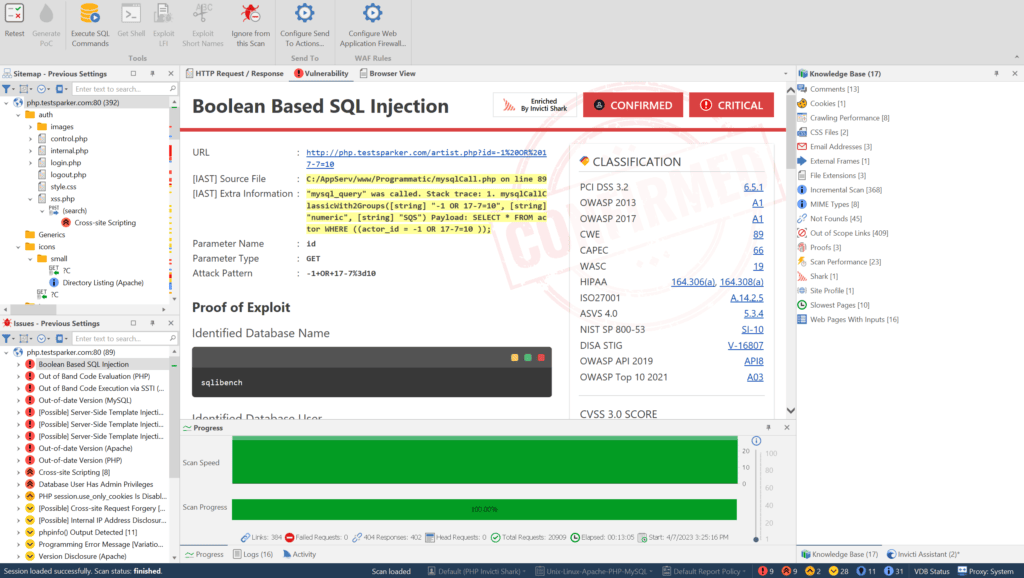
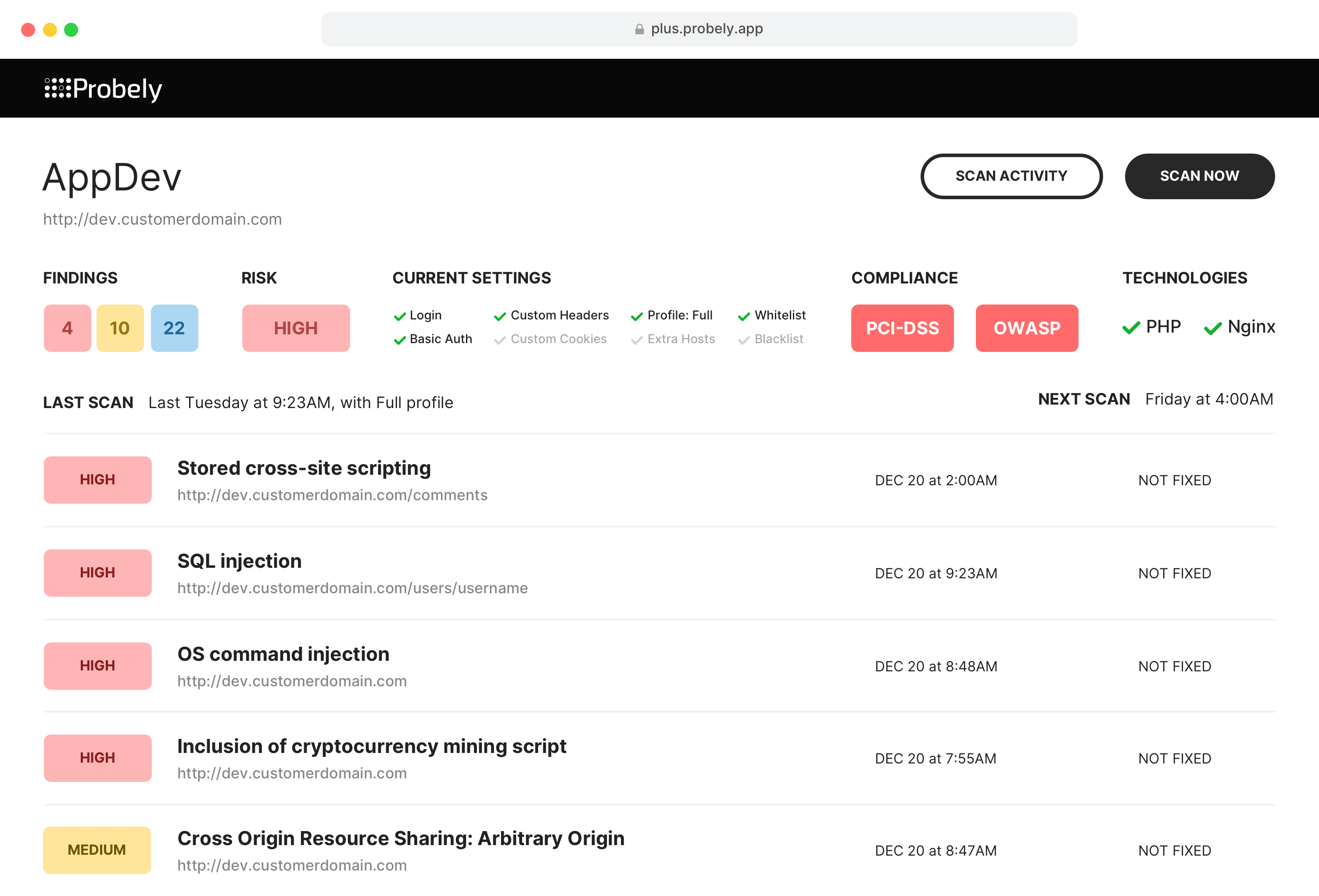
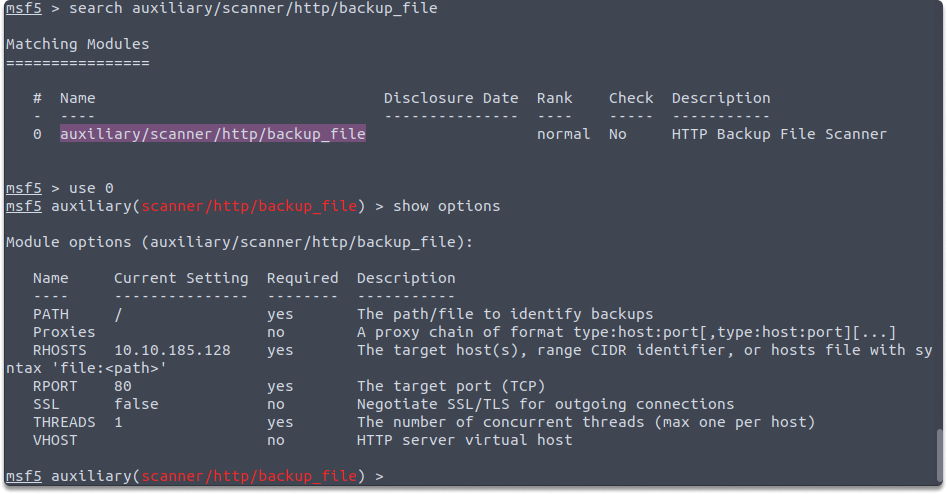
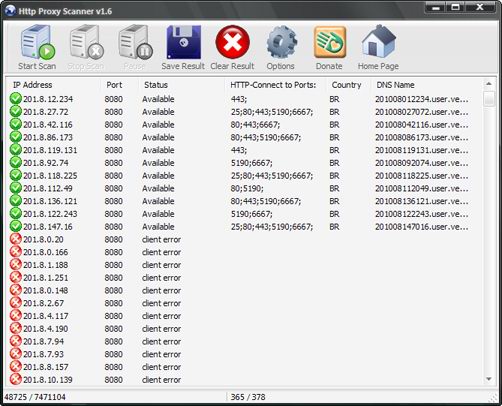
Using HTTP to GET a QR Code. The Response when QR Code is selected from... | Download Scientific Diagram

Amazon.com : NETUM Wireless Wi-Fi 2D Barcode Scanner Connect with TCP UDP Network Protocols, Hands Free Automatic Sensing Bar Code Reader 1D 2D QR pdf417 Scan Gun Suitable for Inventory, POS Industry -
![IIS Short Name Scanner - Scanner For IIS Short File Name Disclosure Vulnerability (using the tilde [~] character) IIS Short Name Scanner - Scanner For IIS Short File Name Disclosure Vulnerability (using the tilde [~] character)](https://4.bp.blogspot.com/-CbD362CSA5M/VsQBC9YqQmI/AAAAAAAAFMY/kyKyV0Mi9Jk/s1600/IIS%2BShort%2BName%2BScanner.png)
IIS Short Name Scanner - Scanner For IIS Short File Name Disclosure Vulnerability (using the tilde [~] character)