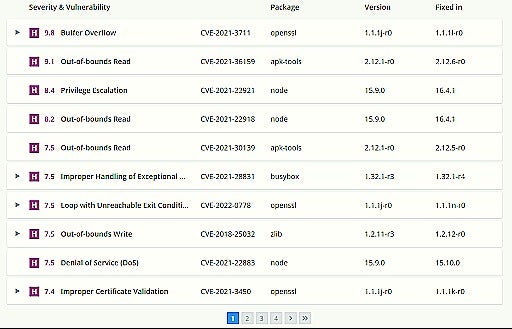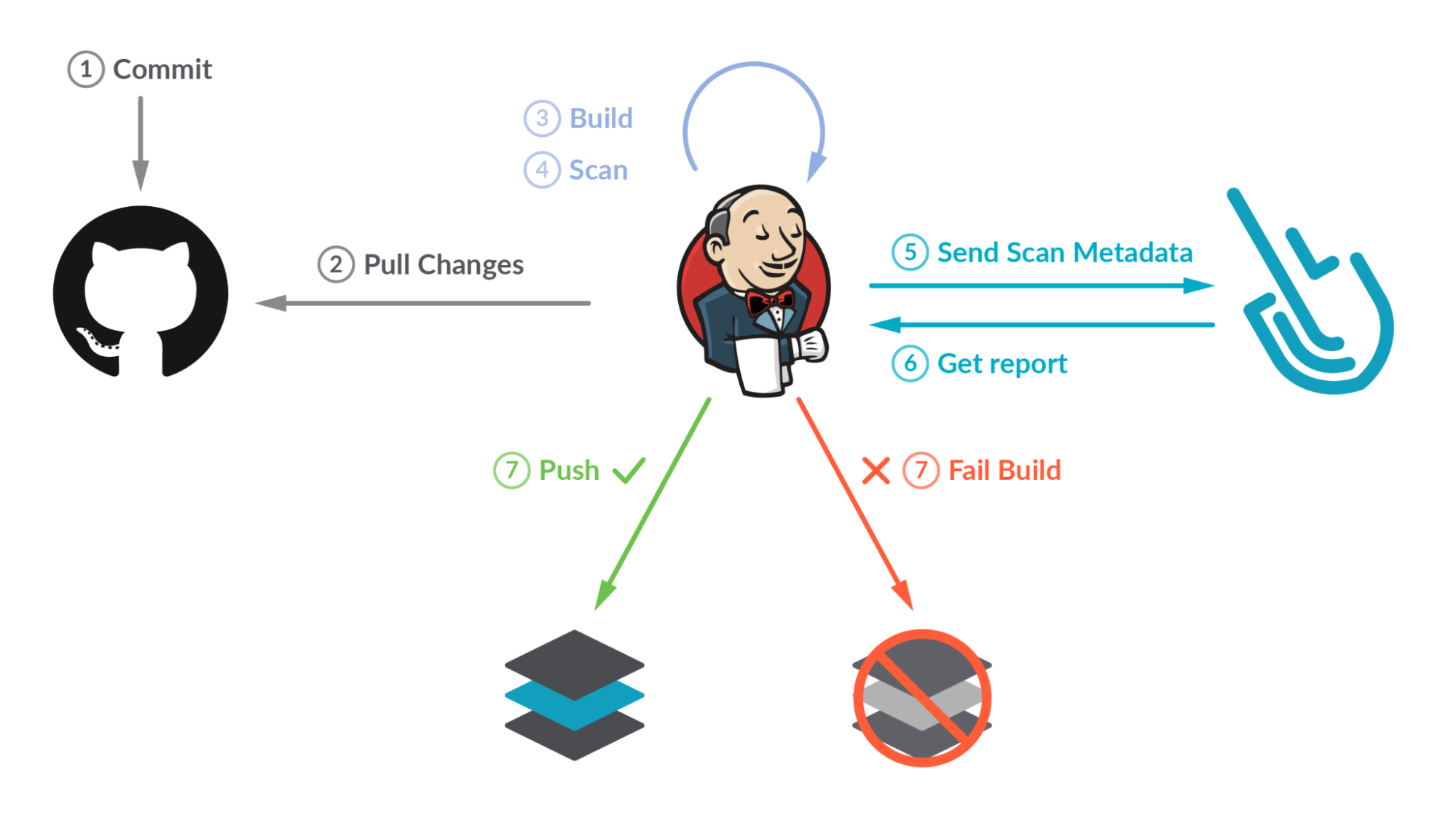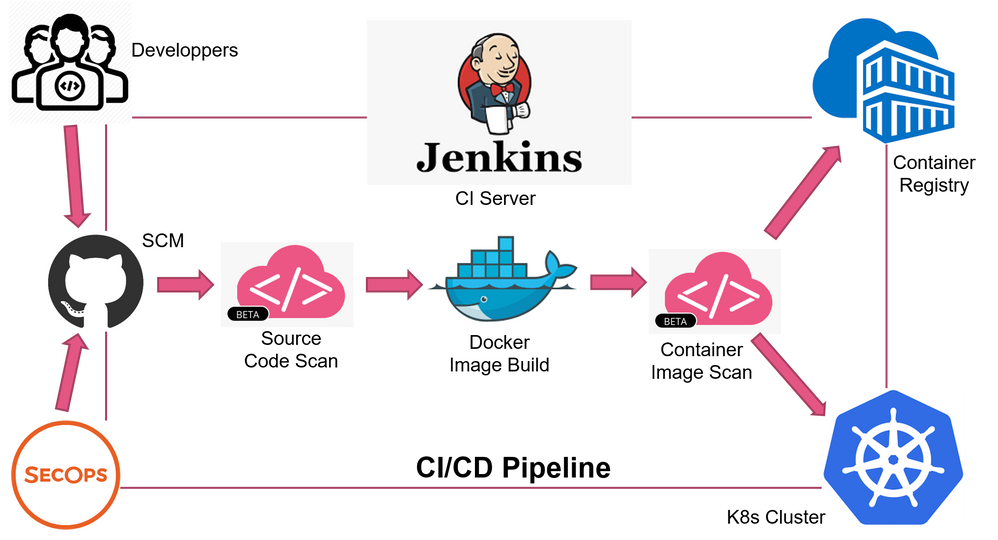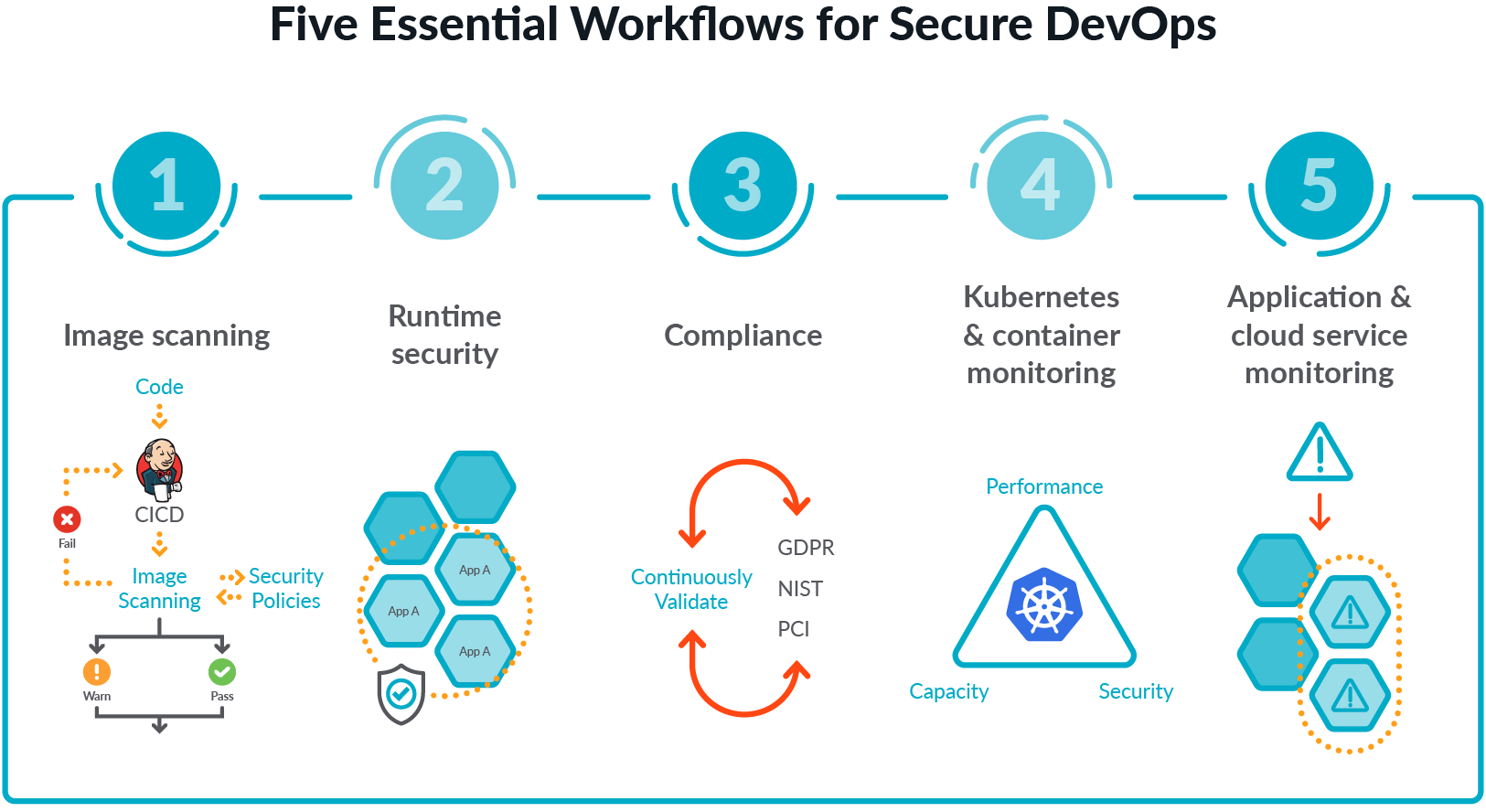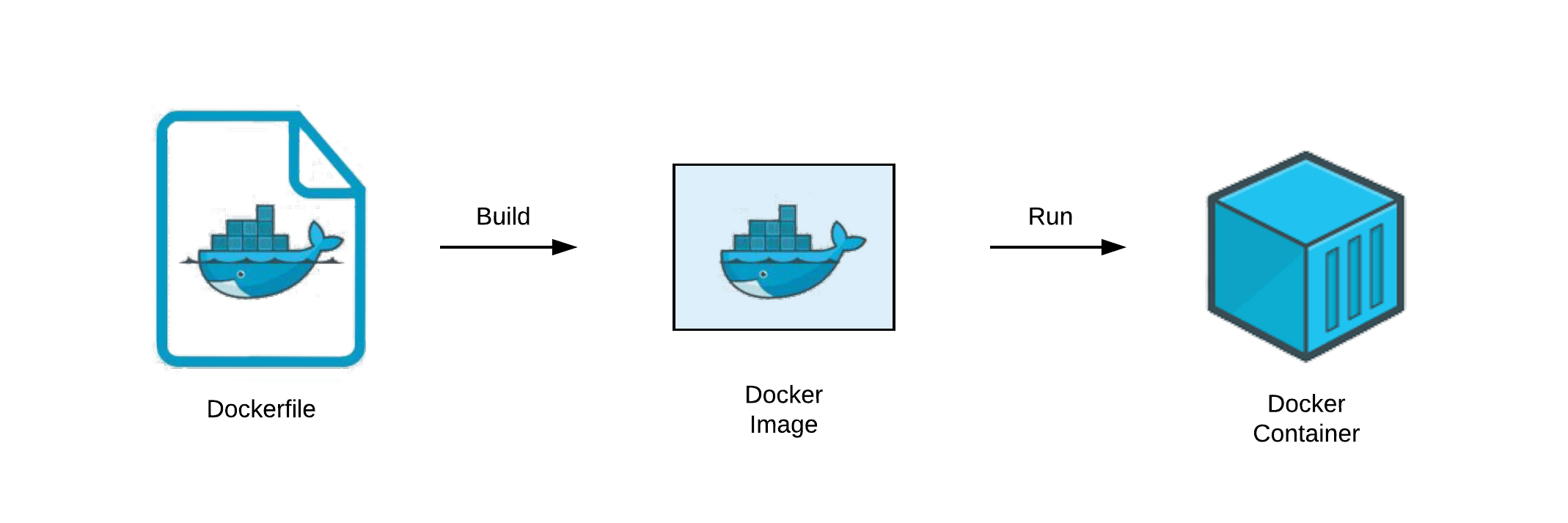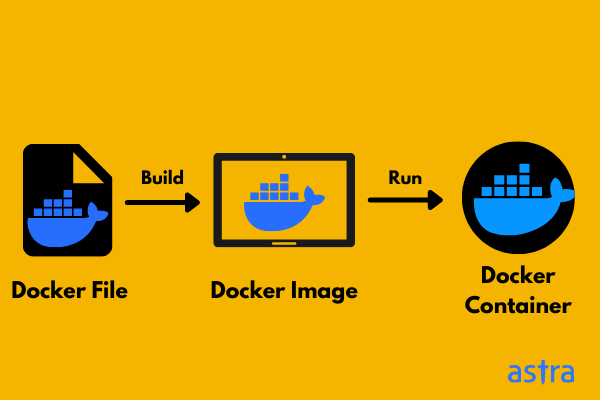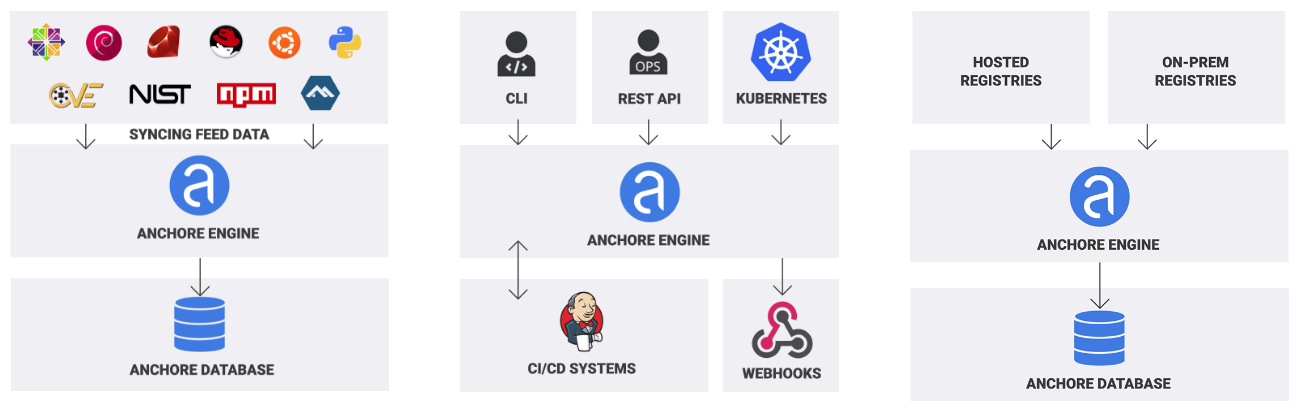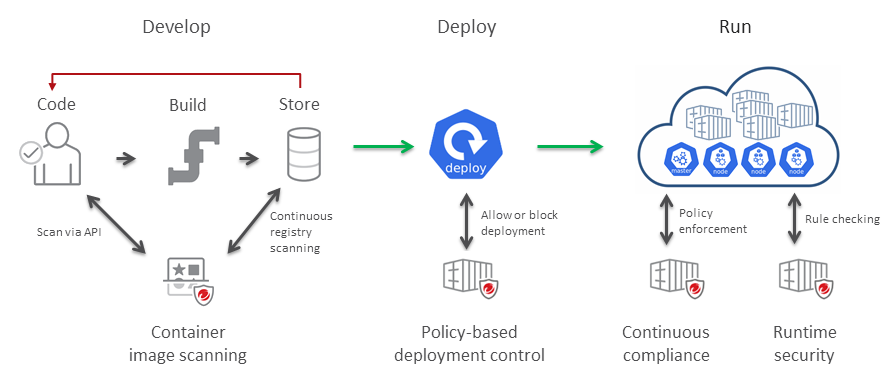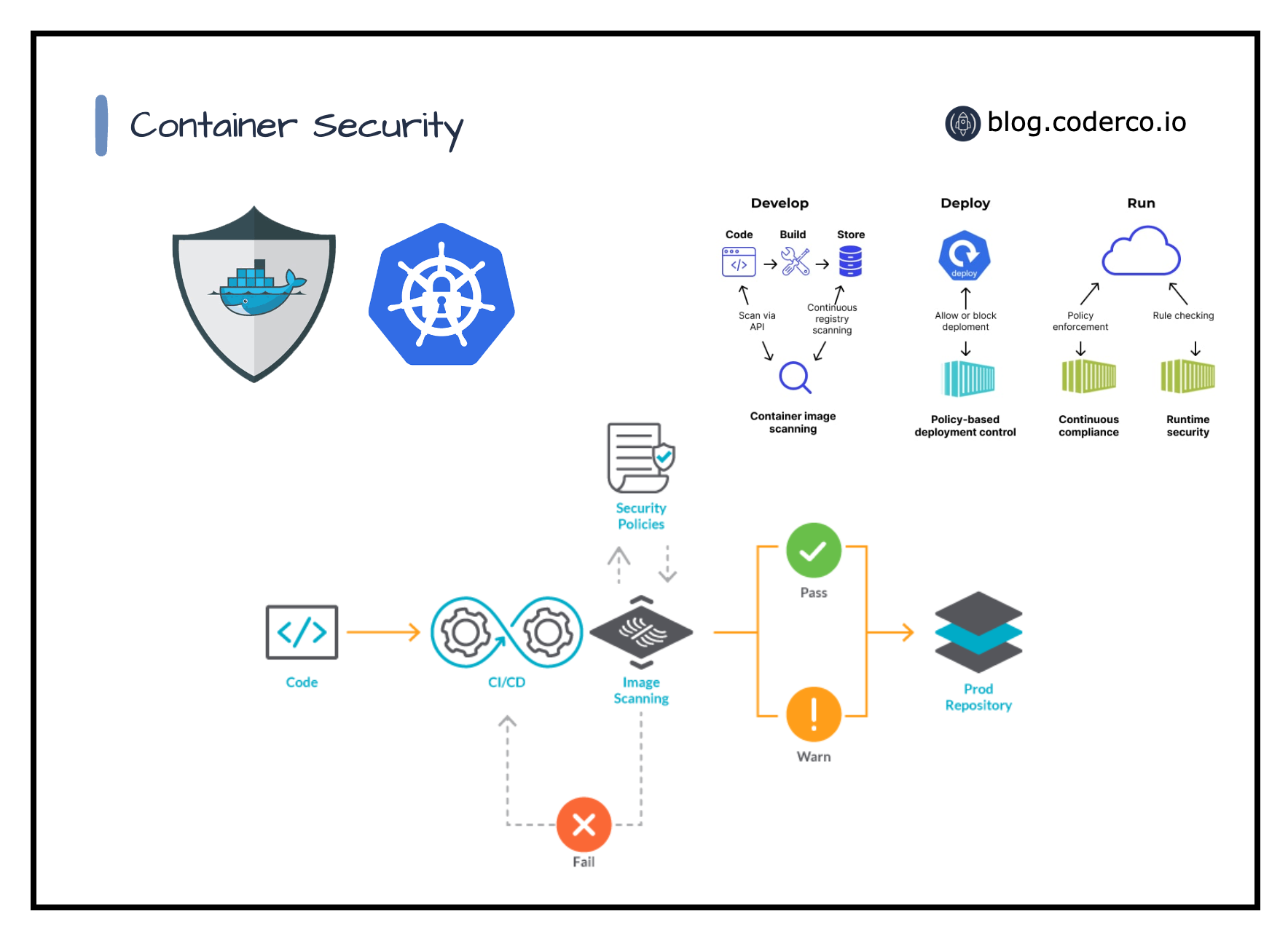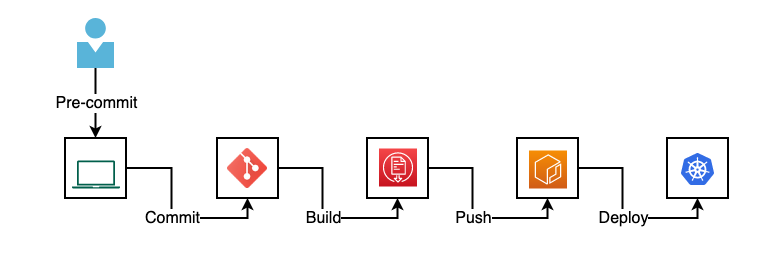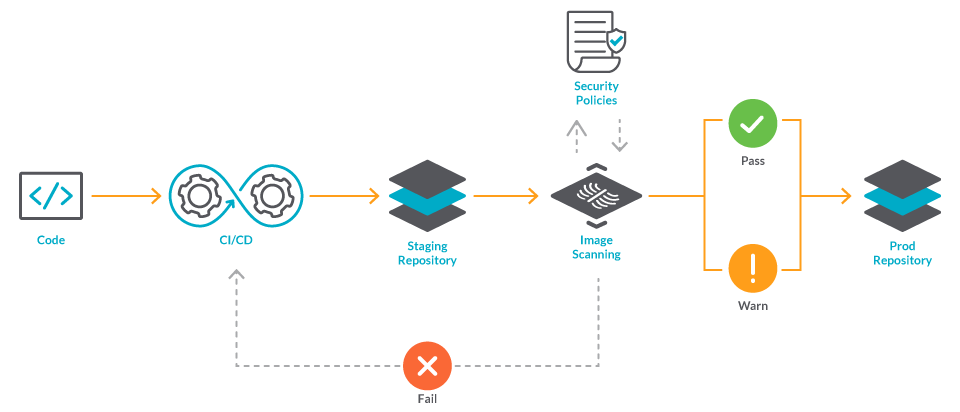
Testing how to use some container vulnerabilities scanners with Azure Pipelines :: my tech ramblings — A blog for writing about my techie ramblings

Scanning Docker Images for Vulnerabilities using Clair, Amazon ECS, ECR, and AWS CodePipeline | AWS Compute Blog
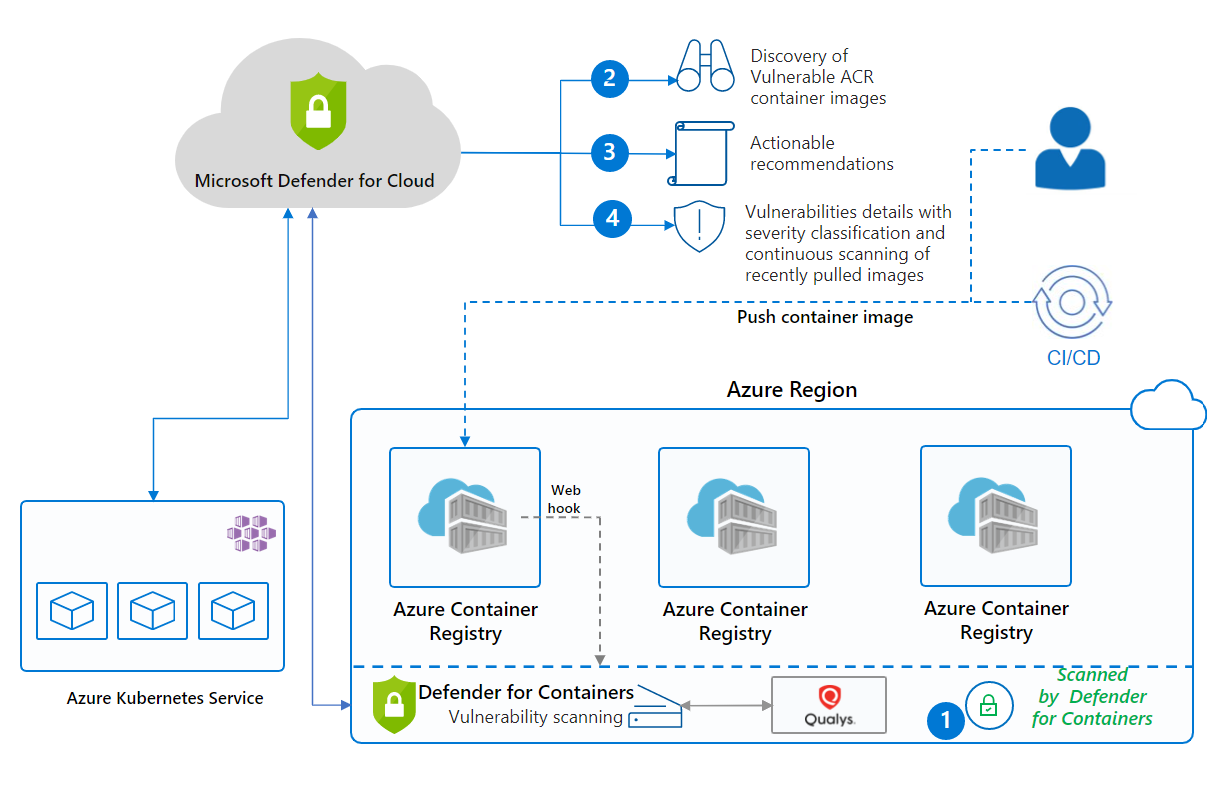
Enhance your CI/CD deployment by using Vulnerability Assessments from Microsoft Defender for ACR - Microsoft Community Hub

How to build a CI/CD pipeline for container vulnerability scanning with Trivy and AWS Security Hub | AWS Security Blog

Hidden gem in Azure: Scan your docker images in ACR, view results in Sub Assessment API and Azure Security Center – SecureCloudBlog